This post continues from our previous discussion, How Government Agencies Benefit from Digital Asset Management – Part 1. Now, let’s dive into how we configured the DAM system specifically to enhance security and ensure compliance for this government agency.
SAML Single Sign-On (SSO)
Each login is authenticated through a centrally managed identity service – WOG Active Directory.
Seamless Login Experience: Users only need to log in once using the same credentials they use daily for their computers. This creates a unified, hassle-free login process.
Automatic Account Deactivation: If a user’s account is expired or disabled in the central identity service (e.g., upon leaving the organisation), their access to the DAM system is automatically revoked, maintaining secure access control.
Two-Factor Authentication (2FA): To further enhance security, users are required to install the Microsoft Authenticator app on their mobile devices. This ensures that logging in includes a second layer of verification for robust protection.
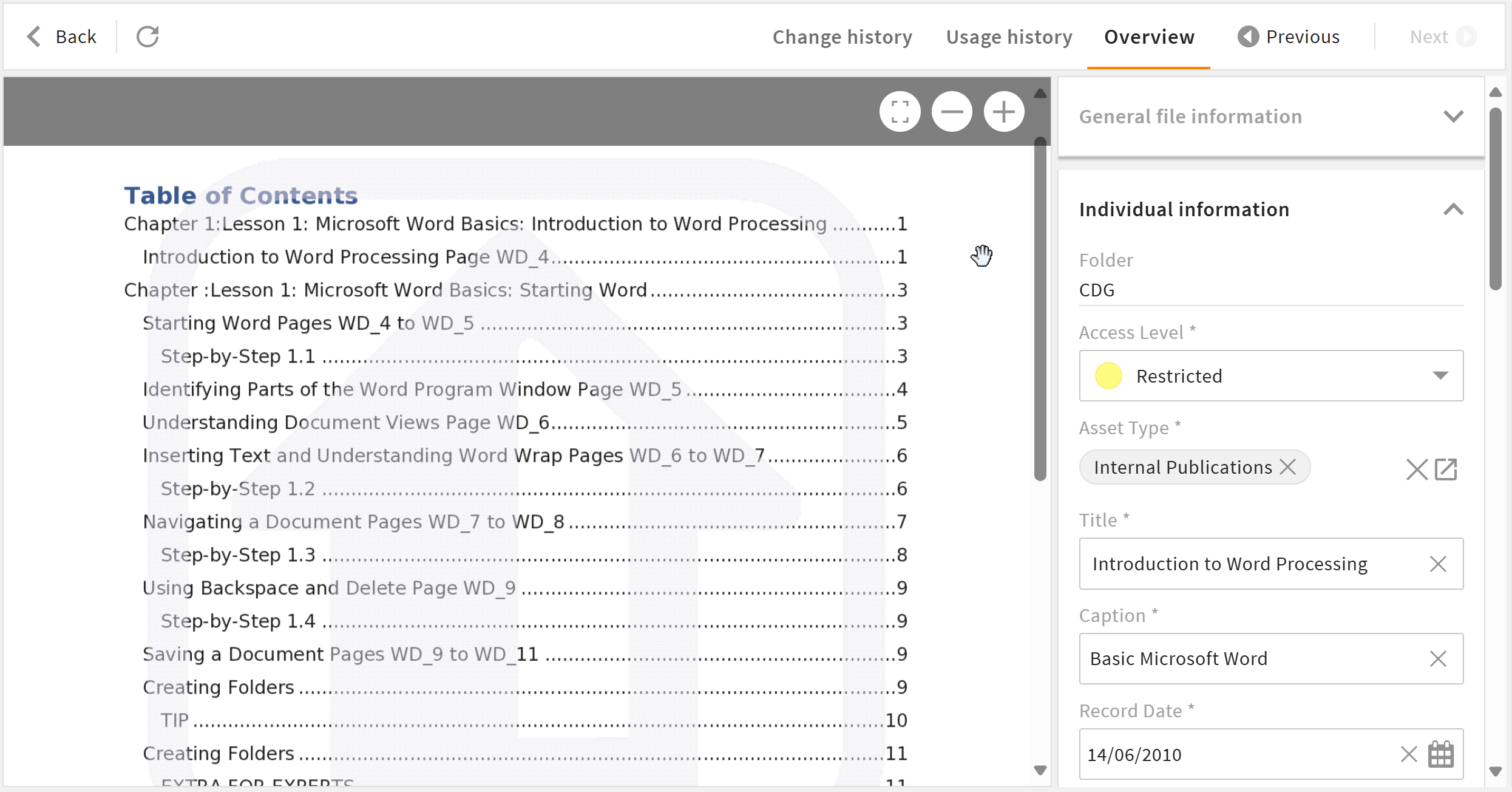
User Roles and Permissions
We configured a role-based system where selected users from each of the 16 departments are assigned specific roles to manage their department’s files:
Administrator: Users with full system access, closely working with the DIW support team to manage and oversee the system.
Editor: Users authorised to upload, delete, and edit files. Editors are responsible for tagging files with relevant metadata like titles, descriptions, keywords, categories, locations, notable persons, etc.
Approver: These users handle requests for file downloads when other users do not have direct download rights.
Viewer: Most users fall into this role, allowing them to view and download files for which they have permission.
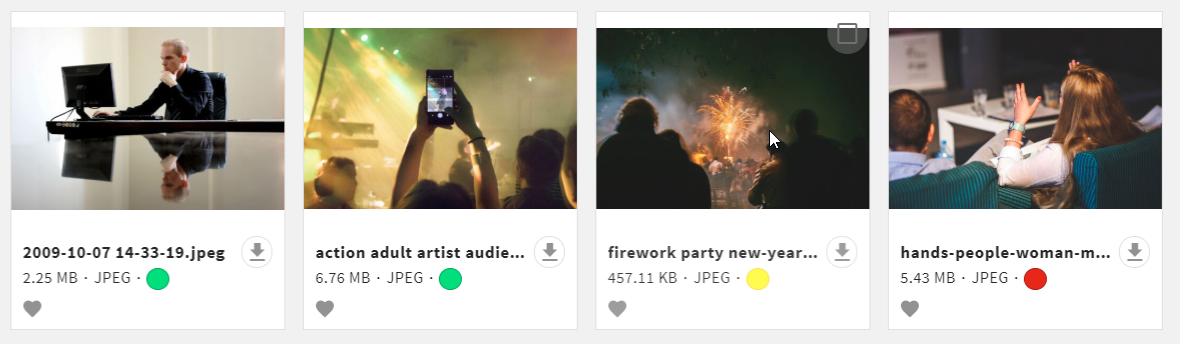
Access Levels
Every file is assigned a specific access level, defining how different user roles can interact with it.
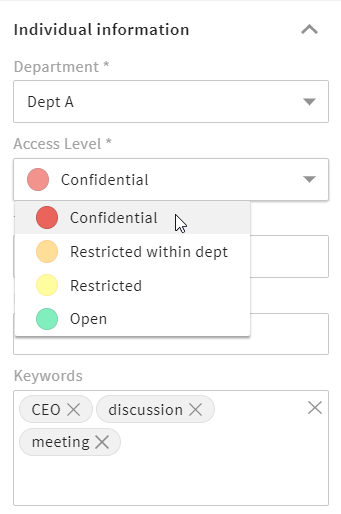
For example, files with restricted access (indicated by a yellow dot ![]() ) can be viewed by all users, but downloading the file requires submitting a request. Only after approval is the download permitted.
) can be viewed by all users, but downloading the file requires submitting a request. Only after approval is the download permitted.
Download Approval Workflow
A key part of maintaining control over file distribution is the download approval workflow.
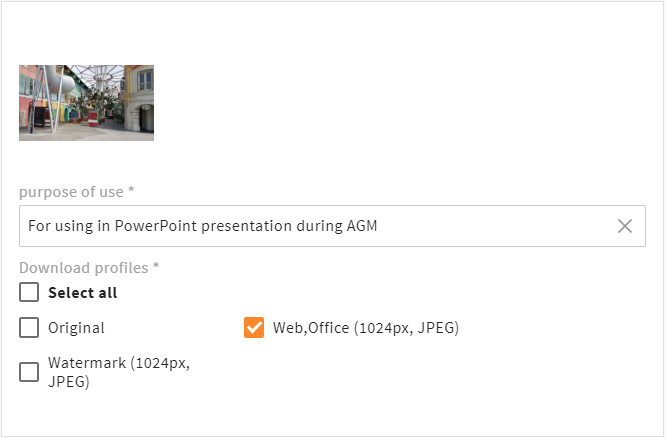
Download requests are automatically routed to the appropriate approver based on file ownership.
Upon approval, the requester receives an email with the download link, ensuring proper authorisation and traceability of file access.
Watermarking
Watermarking plays an essential role in protecting files from unauthorised use and distribution. We have applied different watermarks for distinct purposes:
Preview images with watermarks prevent users from copying or misusing them. This ensures users to follow the formal download approval process.

Downloadable images with red watermarks are designated for print media, such as brochures, publications, and exhibition panels.

Downloadable images with white watermarks are tailored for online usage in presentations, websites, and mobile apps, marking them appropriately for digital distribution.

Document Preview
For multi-page documents, only the first page is available for preview, but the entire document remains fully searchable. This allows users to find relevant information while ensuring that full access is only granted to authorised users.